Custodial Risks and Auditing in WBTC Ecosystem: Ensuring Security and Transparency
History
The consortium behind the Wrapped Tokens initiative, encompassing WBTC, comprised BitGo, Kyber Network, and Ren (formerly known as Republic Protocol). Established by these organizations, the project was inaugurated on October 26, 2018, with its core objective being the creation of an ERC-20 token that could introduce innovative application possibilities for Bitcoin within the Ethereum ecosystem. WBTC endeavours to standardize bitcoins according to the ERC-20 standard, thereby enabling Ethereum-based smart contract developers, decentralized exchange systems, and various components of the Ethereum landscape to directly access Bitcoin's liquidity through a 1:1 pegged coin system.
BitGo, established by Mike Belshe in 2013, operates as an institutional firm providing digital asset custody, trading, and financial services. It stands as one of the driving forces behind WBTC and holds the original role of safeguarding the essential tokens and keys required for WBTC issuance. Created in 2017 by Loi Luu, Victor Tran, and Yaron Velner, Kyber Network functions as an on-blockchain liquidity protocol designed to streamline the integration of cryptocurrency tokens and DeFi applications. Based in Singapore, Kyber Network maintains a partnership with Ren and also operates as a participant in the WBTC network, overseeing the creation and removal of WBTC tokens to maintain a balanced 1:1 ratio with BTC reserves. Ren, established by Taiyang Zhang and Loong Wang in 2017, specializes in cross-blockchain integration of cryptocurrency assets and DeFi applications, providing solutions like RenBridge and RenVM.
In January 2019, the initial whitepaper detailing WBTC was made public, paving the way for the token's launch alongside eight merchant partners: AirSwap, Dharma, ETHfinex, GOPAX, Kyber Network, Prycto, Ren, and Set Protocol. These partners collectively facilitated conversions between Bitcoin and WBTC. Following this launch, numerous prominent organizations in the cryptocurrency domain joined the collaborative endeavour. They became launch partners, aiding in the adoption of WBTC by holding tokens, participating in governance committees, or promoting awareness of the token. Prominent entities among these partners include Gnosis, MakerDAO, Dharma, AirSwap, IDEX, Compound, DDEX, Hydro Protocol, Set Protocol, Radar Relay, Blockfolio, and Prycto.

A prime example of bridging the gap between established financial institutions and the decentralized world in the evolving cryptocurrency industry is Wrapped Bitcoin (WBTC). This token allows users to trade and engage with Bitcoin (BTC) on the Ethereum blockchain, thereby expanding the horizons of decentralized finance (DeFi) applications. However, the reliance of WBTC on custodians for safeguarding the underlying Bitcoin collateral raises substantial concerns related to security, transparency, and audit practices. This piece of writing delves into the potential risks associated with custodians within the WBTC ecosystem underscores the pivotal importance of robust custodial practices and explores strategies for mitigating these risks through thorough audits.
Understanding Custodial Risks
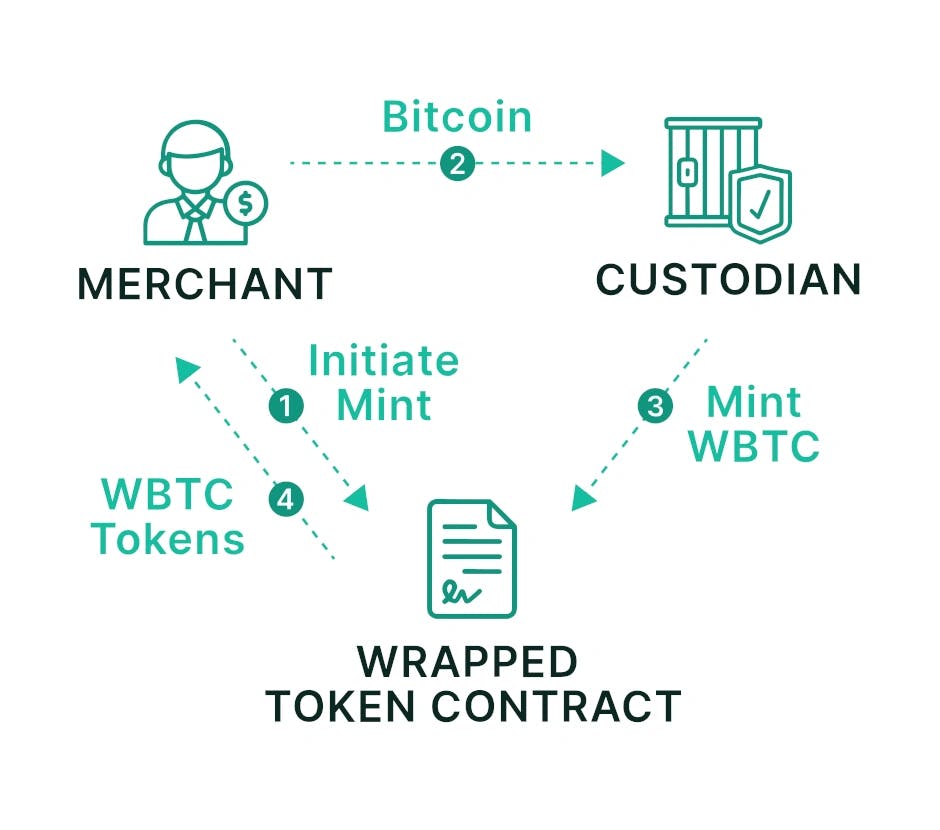
Custodians serve as pivotal entities within the Wrapped Bitcoin (WBTC) ecosystem, tasked with the responsibility of securely storing and safeguarding the Bitcoin collateral that underlies the WBTC tokens. While their role is essential for the functioning of the ecosystem, it's imperative to acknowledge and meticulously analyze the custodial risks that arise when entrusting a third party with valuable assets. These risks encompass a range of technical and operational vulnerabilities that demand thorough consideration. Let's delve into the technical aspects of these custodial risks.
Hacking Risk in Custodial Operations:
Custodians within the WBTC ecosystem manage a complex digital infrastructure that holds valuable Bitcoin collateral, making them prime targets for malicious hackers. The high value of assets, coupled with the allure of potential large-scale gains, makes custodial systems attractive targets for cybercriminals. A successful attack could have dire consequences for the WBTC ecosystem, including the loss of collateral and compromised user assets. Here's a technical breakdown of the hacking risk:
1. Private Key Exposure: The core vulnerability lies in the exposure of private keys. Custodians use private keys to access and control the Bitcoin collateral. If hackers manage to access these private keys, they gain full control over the assets, enabling them to transfer the Bitcoin to their wallets. This could be achieved through various technical means:
Software Vulnerabilities: Identifying vulnerabilities within the custodial software stack, such as the operating system, database, or applications, enables unauthorized access to sensitive information, including private keys. Vulnerabilities may encompass zero-day exploits or unpatched software elements.
Weak Security Configurations: Misconfigurations of security settings, such as improper firewall rules, weak authentication mechanisms, or inadequate encryption, can create openings for attackers to infiltrate the infrastructure and extract private keys.
2. Attack Vectors: Malicious actors can leverage multiple attack vectors to compromise custodial systems and gain access to private keys:
Phishing and Social Engineering: Cybercriminals might employ phishing attacks to trick custodial employees into revealing sensitive information, such as login credentials or private keys. A well-crafted phishing email could deceive employees into thinking they're interacting with legitimate services.
Malware Injection: Injecting malicious code into custodial applications or systems can enable attackers to gain unauthorized access. This can be achieved through techniques like supply chain attacks, where compromised third-party software is used.
Brute Force Attacks: If private keys are stored or transmitted in inadequate formats or are weakly protected, attackers could employ brute force attacks to guess the keys' values.
3. Mitigation Strategies: To counter the hacking risk, custodians must implement robust technical measures that focus on safeguarding private keys and fortifying the overall security posture of their systems:
Hardware Security Modules (HSMs): HSMs are specialized cryptographic devices that securely store and manage private keys. Using HSMs can significantly mitigate the risk of private key exposure, as they are designed to resist physical and logical attacks.
Multi-Signature Wallets: Distributing control over private keys among multiple parties using multi-signature wallets can prevent a single point of failure. A certain number of authorized parties must jointly approve any transaction, enhancing security.
Regular Security Audits and Penetration Testing: Frequent security audits and penetration testing can identify vulnerabilities and weaknesses in the custodial infrastructure. Addressing these issues proactively reduces the attack surface.
Intrusion Detection and Monitoring: Employing intrusion detection systems and continuous monitoring can help detect anomalous activities and potential unauthorized access attempts.
4. Industry Examples: Historical incidents highlight the criticality of addressing hacking risks:
Mt. Gox: One of the most infamous cases involves the hacking of the Mt. Gox exchange in 2014, leading to the loss of over 700,000 Bitcoin. The breach was attributed to technical vulnerabilities and poor security practices.
Operational Failures: Technical systems supporting custodial operations need to be resilient and fault-tolerant. Downtime or operational failures could prevent timely access to the collateral, impacting the ability to redeem WBTC tokens. Employing redundancy, load balancing, and disaster recovery mechanisms are crucial technical strategies to mitigate operational risks.
Fraudulent Activities: Technical controls are essential to prevent custodians from engaging in fraudulent activities. This might include the unauthorized creation of additional WBTC tokens or the misuse of the stored collateral. Implementing cryptographic auditing mechanisms and smart contract controls can help ensure transparency and accountability.
The consequences of custodial failures or vulnerabilities are substantial:
Loss of Funds: A successful hack or exploitation of vulnerabilities can lead to the outright theft of the Bitcoin collateral, causing financial losses to both the custodian and the WBTC ecosystem participants.
Compromised User Assets: Inadequate security measures might expose user assets held within the custodial system. This could result in the loss of individual holdings and erode confidence in the system's security.
Loss of Trust: Custodial failures can undermine trust in the DeFi ecosystem as a whole. Users may become hesitant to participate in WBTC-related activities, impacting the ecosystem's growth and sustainability.
Lessons from Custodial Failures
Centralized Custody Risks: Mt. Gox Exchange Hack: In 2014, the Mt. Gox exchange hack marked a pivotal occurrence in cryptocurrency history. The exchange, which had held the position of the world's largest Bitcoin exchange, experienced a substantial security breach that led to the theft of around 850,000 BTC, valued at billions of dollars during that period. This event underscored various essential takeaways:
Centralized Vulnerabilities: Centralized exchanges hold private keys to users' funds, making them attractive targets for hackers. If the exchange's security measures are compromised, attackers gain access to a vast number of assets.
Lack of Transparency: Mt. Gox's inadequate transparency regarding its financial health and the security measures it employed exacerbated the crisis. Users were left in the dark about the actual state of their funds.
Regulatory and Legal Implications: The Mt. Gox collapse triggered legal battles and regulatory scrutiny. The situation raised questions about the regulatory framework for exchanges and the responsibilities they have toward their users' funds.
Market Confidence: The hack eroded trust in the entire cryptocurrency ecosystem. The subsequent decrease in market confidence had a significant impact on cryptocurrency valuations.
Decentralized Finance (DeFi) Vulnerabilities: More recently, the rise of DeFi platforms has introduced a new set of custodial challenges, albeit in a different context. DeFi protocols aim to provide financial services without intermediaries, but they also bring new risks:
Smart Contract Risks: DeFi platforms heavily rely on smart contracts for their operations. Vulnerabilities in smart contracts can lead to exploits, where malicious actors manipulate the contract's logic to drain funds.
Impermanent Loss and Yield Farming: DeFi offers opportunities for yield farming and liquidity provision, but these activities come with risks like impermanent loss. Traders can suffer losses due to the price volatility of assets in liquidity pools.
Decentralization vs. Centralization: While DeFi is designed to be decentralized, many DeFi platforms still have centralized components, such as governance mechanisms. These can introduce single points of failure or vulnerabilities.
User Education: DeFi introduces complex financial concepts and tools to a broader audience. A lack of understanding can lead to users making mistakes or falling victim to scams.
Proactive Risk Mitigation Strategies: In response to these lessons, the cryptocurrency community has been working on proactive risk mitigation:
Security Audits: DeFi protocols increasingly undergo thorough security audits by independent experts to identify vulnerabilities and mitigate risks in smart contracts and codebases.
Multi-Signature Wallets: Exchanges and custodians are implementing multi-signature wallets, demanding multiple private keys for fund access. This approach diminishes the vulnerability of a solitary point of failure.
Decentralization Efforts: DeFi projects are working on increasing decentralization in both governance and technical infrastructure to reduce susceptibility to attacks.
Insurance: Some exchanges and DeFi protocols are exploring insurance options to compensate users in case of security breaches.
User Education and Awareness: The community is focusing on educating users about security best practices, such as using hardware wallets, employing strong authentication, and avoiding risky behaviours.
The Imperative of Transparent Security Measures
In the rapidly evolving landscape of cryptocurrency and blockchain technology, security has become a paramount concern for both individuals and institutions participating in the ecosystem. This is especially true for assets like Wrapped Bitcoin (WBTC), which is a tokenized version of Bitcoin backed 1:1 by real Bitcoin. Considering the financial significance and decentralized attributes of these assets, emphasizing transparent security measures holds paramount importance in guaranteeing the trust and confidence of stakeholders.
1. Inherent Risks: A variety of risks, including hacking, fraud, theft, and operational vulnerabilities, can affect cryptocurrencies and blockchain assets. The inherent immutability and pseudonymity of blockchain transactions, though advantageous, can transform into a vulnerability if not properly handled. As the value of assets like WBTC rises, they draw the attention of malicious actors who aim to capitalize on vulnerabilities and purloin funds.
2. Trust and Accountability: Transparency in security practices is a cornerstone of building trust and accountability within the WBTC ecosystem. When users know that robust security measures are in place and that their assets are safeguarded, they are more likely to feel confident in utilizing these assets for various purposes, such as trading, lending, or collateralizing. This trust encourages participation and investment in the ecosystem, ultimately driving its growth.
3. Multi-Layered Security Protocols: To ensure the security of WBTC and other digital assets, custodians – entities responsible for holding and managing these assets on behalf of users – must implement multi-layered security protocols:
Cold Storage Solutions: The majority of funds should be stored in offline or "cold" wallets, which are not connected to the internet. This drastically reduces the risk of online attacks.
Hardware Security Modules (HSMs): HSMs are specialized hardware devices engineered to manage and protect cryptographic keys. They establish a secure environment for handling key management and cryptographic tasks, rendering unauthorized access to sensitive data exceedingly challenging.
Multi-Signature Wallets: To authorize transactions, multi-signature wallets necessitate several private keys. This introduces an additional security layer by guaranteeing that no single person can unilaterally access or transfer funds.
Robust Access Controls: Access to sensitive systems and assets must be tightly controlled through authentication mechanisms, strong passwords, and perhaps even biometric identification.
4. Regular Security Assessments: The landscape of cybersecurity is ever-evolving, and new vulnerabilities and attack vectors are constantly emerging. To stay ahead of potential threats, custodians must conduct regular security assessments, including penetration testing and vulnerability assessments. These assessments involve attempting to breach systems and identify weaknesses in a controlled environment, allowing for timely mitigation measures to be taken.
5. Data-Driven Decision Making: Data and metrics play a crucial role in understanding the effectiveness of security measures. Monitoring and analyzing data related to attempted breaches, successful attacks, and security incidents can provide valuable insights into the areas that require improvement.
The Role of Auditing
Auditing plays a crucial role in ensuring the security and collateralization of Wrapped Bitcoin (WBTC) assets held by custodians. WBTC represents a tokenized iteration of Bitcoin within the Ethereum blockchain, with custodians tasked with safeguarding the real Bitcoin-supporting WBTC tokens. Auditing in this scenario primarily aims to verify the precision and security of custodians' holdings, methodologies, and compliance with industry norms. Let's delve into the technical facets:
Verification of Asset Holdings: Auditing involves verifying the custodians' claims of holding a certain amount of Bitcoin as collateral for the issued WBTC tokens. This is typically done through a combination of blockchain analysis and verification of cold wallet addresses. Cold wallets are secure, offline storage solutions commonly used to hold cryptocurrencies safely. Auditors analyze the blockchain to ensure that the number of WBTC tokens in circulation is indeed backed by an equivalent amount of actual Bitcoin stored in the custodian's cold wallets.
Security Practices Assessment: Auditors assess the custodians' security practices to ensure that the Bitcoin reserves are adequately protected against theft, hacks, and other security risks. This involves evaluating the custodians' multi-signature setups, hardware security modules (HSMs), encryption protocols, access controls, and overall network security measures. The goal is to identify vulnerabilities that could potentially compromise the integrity and security of the WBTC collateral.
Compliance with Industry Standards: The auditors review whether the custodians are following industry best practices and complying with established standards for cryptocurrency custody and security. This might include adherence to frameworks like ISO 27001 for information security management or the CryptoCurrency Security Standard (CCSS) specifically designed for the crypto industry. Compliance ensures that the custodians are taking appropriate steps to safeguard the assets.
Independent Third-Party Verification: The audits are conducted by reputable third-party firms that specialize in cybersecurity and cryptocurrency audits. These firms are independent of the custodians, which adds credibility to the audit results. Independent verification reduces the likelihood of conflicts of interest and provides an unbiased assessment of the custodians' practices.
Transparency and Information Asymmetry: Audits offer transparency to various stakeholders, including the WBTC community, investors, and regulatory bodies. By making the audit reports publicly available, interested parties can gain insights into the security measures and collateralization status of the WBTC ecosystem. This transparency helps to bridge the gap of information asymmetry, where certain parties might have more information than others, and contributes to building trust in the system.
Confidence Building: The entire auditing process enhances the overall confidence in the WBTC ecosystem. Investors can be more assured that their investments are backed by real assets, and regulators can have a clearer picture of the security measures in place. This increased confidence can lead to a more robust and stable WBTC market.
Mitigating Counterparty Risk
Mitigating counterparty risk is crucial in the context of custodianship, where assets like Wrapped Bitcoin (WBTC) are held by third-party custodians. Counterparty risk refers to the potential for a custodian to fail in its responsibilities, leading to potential loss or compromise of the assets held. To mitigate this risk, it is advisable to adopt a multi-custodian approach. Let's explore the technical intricacies:
Diversification of Custodians: Instead of relying on a single custodian, the strategy involves engaging multiple custodians to hold and secure the WBTC assets. Each custodian operates independently, holding a portion of the total WBTC collateral. Diversification reduces the concentration of risk associated with a single entity. If one custodian were to fail or face security breaches, the overall impact on the WBTC ecosystem would be limited, as the assets held by that custodian represent only a fraction of the total reserves.
Centralization Concerns: Relying solely on a single custodian centralizes the control and risk. In a centralized model, the failure of that custodian could have severe consequences for the entire ecosystem. It has the potential to cause significant disruptions, erode confidence, and result in potential asset losses. A vulnerability that malicious actors can exploit lies in having a single point of failure.
Distribution of Risk: Distributing the counterparty risk across multiple entities is the essence of a multi-custodian approach. If one custodian encounters issues, the remaining custodians continue to operate independently, maintaining the security and integrity of their respective holdings. This distribution of risk reduces the potential impact of a single failure on the overall ecosystem.
Promoting Competition and Security Standards: When multiple custodians are involved, healthy competition emerges. Custodians strive to maintain the highest security standards and operational efficiency to attract and retain clients. They need to demonstrate their competence in securing assets and adhering to industry best practices. This competition benefits the WBTC ecosystem by driving custodians to continually improve their security measures.
Technical Implementation: Implementing a multi-custodian approach involves distributing the WBTC assets among different custodians. Each custodian manages its allocated assets independently, employing its security protocols, cold storage mechanisms, and access controls. The key technical challenge lies in coordinating custody and security practices across multiple entities while ensuring smooth asset management and operational effectiveness.
Data Management and Reporting: A technical aspect of the strategy is the establishment of a reliable data management and reporting system. The custodians' actions, holdings, and security measures need to be transparently tracked and reported. This requires robust data infrastructure and potentially the use of blockchain technology to maintain an immutable record of asset movements and custody activities.
Frequent and Rigorous Audits
Frequent and rigorous audits play a critical role in maintaining the health and integrity of the Wrapped Bitcoin (WBTC) ecosystem. These audits encompass both financial and security aspects, aiming to verify the custodian's financial stability, the security of underlying assets, and the overall adherence to industry standards. Here's a technical breakdown:
Financial Health Audits: Financial audits involve assessing the custodian's financial statements, transactions, and reserves to ensure that the collateral supporting WBTC tokens is maintained at sufficient levels. This involves analyzing the custodian's balance sheets, income statements, and cash flow statements. The objective is to verify that the custodian has the necessary assets to cover the outstanding WBTC tokens in circulation. This is especially crucial because the value of WBTC is pegged to the value of Bitcoin, and any discrepancies could lead to systemic issues.
Security Audits: Security audits evaluate the custodian's security practices and measures in place to safeguard the underlying Bitcoin assets. This entails thoroughly assessing the custodian's security protocols, multi-signature configurations, cold storage systems, encryption techniques, access controls, and network structure. The objective is to detect vulnerabilities and potential paths for attacks that might jeopardize the assets' integrity and accessibility.
Regular Auditing Frequency: The phrase "frequent audits" signifies that these evaluations occur regularly, as opposed to being isolated occurrences. The frequency could be defined based on industry best practices, regulatory requirements, and the evolving threat landscape. For instance, audits might be scheduled quarterly or semi-annually. Regular audits ensure that the custodian's practices are continuously evaluated and adapted to changing security threats.
Transparent and Comprehensive Auditing: Transparency is key to building trust in the WBTC ecosystem. Audits must encompass a comprehensive and transparent process, encompassing meticulous documentation of audit procedures, methodologies, findings, and recommendations. This transparency empowers stakeholders to grasp the extent of the audits and the steps implemented to rectify any identified concerns.
Independence and Impartiality: To ensure the credibility of the audit process, audits must be conducted by independent third-party experts. These experts have no direct affiliation with the custodian, ensuring impartiality in their assessments. Independence minimizes potential conflicts of interest and enhances the credibility of the audit results.
Technical Expertise and Tools: Auditors need technical expertise in blockchain technology, cryptography, and cybersecurity to effectively assess the security measures and practices in place. They may use specialized tools for analyzing blockchain transactions, evaluating cryptographic implementations, and identifying vulnerabilities in the custodian's systems.
Audit Report and Recommendations: The audit procedure ought to conclude with a comprehensive report outlining the audit's scope, employed methodologies, findings, and recommendations. This report functions as a point of reference for stakeholders, encompassing investors, regulators, and the WBTC community, to grasp the custodian's security and financial stance.
Conclusion:
In the dynamic landscape of cryptocurrency and blockchain technology, the Wrapped Bitcoin (WBTC) initiative exemplifies how innovation connects established financial institutions with the decentralized realm. WBTC empowers users to trade Bitcoin on the Ethereum blockchain, broadening the scope of decentralized finance (DeFi) applications. Yet, concerns arise due to the dependence on custodians to safeguard Bitcoin collateral, triggering apprehensions about security, transparency, and audit practices.
This article delves into comprehending custodial risks, identifying hacking vulnerabilities, and stressing the necessity of transparent security measures. Past instances of custodial failures, both centralized and within the emerging DeFi sphere, underscore the significance of robust security practices and proactive risk-mitigation tactics. Auditing, covering both financial health and security aspects, emerges as pivotal in fostering trust, transparency, and accountability within the WBTC ecosystem.
As the embrace of WBTC and similar ventures gains momentum, the collaborative endeavours of industry stakeholders, custodians, auditors, and the broader cryptocurrency community emerge as essential. By tackling technical hurdles and risks tied to custodianship via meticulous audits, transparent security protocols, diverse custody approaches, and multi-custodian strategies, the cryptocurrency realm can navigate the intricacies of integrating traditional financial assets into the decentralized landscape. Through these measures, the WBTC ecosystem can strive to achieve a dynamic equilibrium between innovation, security, and trust, propelling the industry forward.
I'd love to connect with you on Linkedln | Twitter | Github.
Looking forward to catching up with you in my next blog article! Take care and have a great day! 😊
